Content
More importantly, these stocks are outpacing the returns these leading crypto assets aren already producing. Click here to get the full story … along with our long list of backdoor Bitcoin strategies. “Besides slowing down PCs and servers, cryptomining malware can spread laterally once inside the network, posing a major security threat to its victims.
In the world of fee compression, a market access area charging two to three times or more the average cost of an ETF has to be a breath of fresh air for those who run an investment businesses. So far, CoinFlip has rolled out over 1,000 ATMs across the US and supports 10 major cryptocurrencies.
For now, he and his firm are only able to offer an crypto index fund for advisors trying to meet client requests for bitcoin exposure. There’s also the quasi-closed-end fund that holds bitcoin, the Grayscale Bitcoin Trust in the U.S., which has attracted $8 billion in AUM from investors comfortable with paying a 2% expense ratio on top of a 20% premium to net asset value. And of course, there are many platforms you can buy and sell bitcoin on, and some are reputable, such as Coinbase, but there are many operating on the fringes with creaky security and questionable oversight. “Creating strong consumer protections will keep bad actors from competing with legitimate products and help the crypto industry to gain legitimacy in the general public’s eyes,” said Weiss. This is in part because Bitcoin and Blockchain are still tied in the public imagination to money laundering and illicit finances. Anonymous transactions bring to mind headlines about dark web operations and backdoor financing.
“When people talk about cybersecurity, they imagine the film version of it,” said Halliwell. Scenarios that involve someone sneaking into a building through the backdoor, then hacking into the system from a dark room where they quickly crack the password are “probably not the reality”. More likely, he said, is through ‘smishing’, where you receive a spam text message containing a malicious link, that once clicked on, can hack private information; or finding a random USB on the floor, which if you stick into your laptop will download a virus. In the news, look no further than the recent Microsoft Exchange hack, which saw hackers attack holes in the email server. To further strengthen cross-jurisdiction collaboration we will soon be announcing an intelligence alliance.
Backing up the wallet and storing it on an encrypted disk image is a common recommendation given to users, and as development of the Bitcoin client progresses and newer versions are released, the option to encrypt the wallet has been introduced into the software, as shown in Figure 5. So the rising interest from media and business, and increasing trust in the Bitcoin system has seen it become a legitimate currency that has a multitude of supporters behind it. These supporters, however, are not always backing the system for honest reasons. Abuse of the Bitcoin system can come in many different flavours, ranging from individuals over-zealous in their bitcoin-mining endeavours, to security breaches resulting in the loss of thousands of bitcoins, and criminal elements using the currency to fund their underground activities. A Bitcoin user can configure their Bitcoin client to act as a server and listen for incoming JSON-RPC connections from the local host. The bitcoin miner, which can run on the local machine or a remote one, is then configured to send getwork requests to the server. To throw more muscle at the hash calculations, many Bitcoin users also set up mining rigs with high specification systems dedicated to mining.
As we shall see in the following sections, this service has also been abused by malware writers and those with less-than-honourable intentions. The value of the bitcoin currency can vary depending on the exchange used, but the most widely used exchange, Mt. Gox , provides a good indication of its value since the exchange was launched on 18 July 2010. The chart in Figure 2, obtained from the Bitcoin charts website , tracks the value of a BTC, in US dollars, from July 2010 to this day. BY can now transfer the received bitcoin using their matching private key.
I expect the market to get cheaper over time as it gets more established and significant. There’s no reason that crypto will avoid the fee compression we’ve seen in other areas of the market; it’s going to come. And I expect, as we discussed, for us to move progressively toward better and better product structures. These efforts to support consumers and keep illicit entities out of the cryptocurrency system require a clear legal framework.
Detection Of Vulnerabilities In Web Applications By Validating Parameter Integrity And Data Flow Graphs
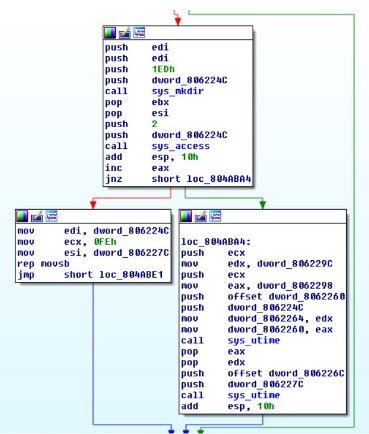
Prometei will also attempt to propagate to systems on the network using the same set of exploits used to gain initial access. A modified version of the Mimikatz credential stealer is also used to obtain SMB or RDP account details which can then be used for lateral movement. There is also evidence Prometei’s operators are attempting incorporating SMBGhost and SMBleed exploits. However, at the time of publication, no exploits for these vulnerabilities have been observed in Prometei’s attack chain. Prometei’s operators gain access to new target networks using a combination of RDP and SMB exploits, including EternalBlue, as well as stolen credentials. If successful, they then use PsExec and WMI to download and install Prometei. First observed in March 2020, Prometei is a modular worm and botnet targeting exposed Windows servers globally.
This coin how to make bitcoin mining profitable is it profitable to mine any cryptocurrency anymore created as a joke so it should …. For now, we only know the expected date and that there will be supply of 21, of GOD circulating and that currency will have no premine. The developers of Super Bitcoin plan is to utilize smart contracts that can be found in Ethereum. Vendio implements a proprietary tagging algorithm appended to a piece of video content at specific times during a specific video duration, selected by the publisher.
To break that down, it’s similar to an ETF in that it trades on a public exchange and people can create new shares of it on an ongoing basis. It’s different in that, as you can see, it can trade to substantial premiums and discounts. This is a model that was pioneered by Grayscale, which is another crypto asset manager, with a fund called GBTC, which many people are probably familiar with. I could rattle off the terms and exemptions under which it exists from a regulatory perspective, from the SEC and FINRA, etc., but they wouldn’t mean much to you.
Stock Market And Paramount
After this point, transactions will still need to be verified, but a miner that solves a block will only be rewarded with bitcoins if the block contains transaction fees specified by transferors . Nakamoto set it up this way to control the total currency generated in the network, so that by 2040 no more than 21 million bitcoins in total will be in circulation. At the time of writing, 183,249 blocks have been solved, meaning approximately 9.1 million BTCs are in circulation. The Bitcoin wallet contains a public and private key pair, as mentioned previously, as well as an address created each time a transaction occurs. Because a new address is generated for each transaction, the wallet can contain many addresses and key pairs. So, a Bitcoin user having X number of bitcoins in their wallet really means they have in their wallet one or many Bitcoin addresses, and a corresponding private key that is needed to resend the bitcoins sent to that address. This also means that anyone can spend the bitcoins sent to the Bitcoin user’s address if they have access to their address and its corresponding private key.
Coinfirm maintains a dedicated department to monitor darknet flows from more than 1,500 cryptocurrencies and protocols. Monitoring of blockchain addresses enables our network to shut off malicious actors’ revenue streams and operating webs.
The Alureon Gang Set Their Eyes On The Bitcoin Prize
And at times, this fund traded 200% above net asset value, which is dripping with crazy sauce. To its credit, Bitwise hasn’t shied away from the premium that the fund’s structure has created. It tweets it out to very little backlash, and in fact got more “likes” than I would expect.
The spate of attacks cost the National Health Service £92m, disrupted 1% of all care and infected 200,000 computers. REvil, Sodinokibi, Nemty, Nephilim, NetWalker, DoppelPaymer, Ryuk, Maze, CLOP, Tycoon and Sekhmet – brand names to a malicious few, fear inciting to everybody else – were some of the top ransomware viruses last year. According to Kroll – Coinfirm’s strategic partner in forensic crypto-crime investigations – the threat was the most observed year-to-date of cyber incident response cases, accounting for over one-third of all. Ransomware, malicious software that infects your computer and displays messages demanding a fee to be paid in order for your system to work again is a class of malware installed through deceptive links in an email, instant message or from visiting the wrong website.
“That’s why we’re focusing on behaviour as much as physical infrastructure,” said Halliwell. As such, law firms will often conduct a lengthy procurement process involving heavy due diligence into potential cloud suppliers, to ensure their privacy concerns are met before any client data is actually put into a platform, Sanders added. So, with lawyers in lockdown working beyond the confines of brick-and-mortar offices, law firms have had to figure out how to make privileged data accessible online — and fast. One solution has been cloud-based computing, which allows lawyers in different locations to collaborate on projects and share sensitive information online. This is a relatively new concept for law firms, explained Joe Cohen, a practice development and innovation manager at Dentons. Often described as the ‘soft underbelly’ of professional services, law firms hold colossal amounts of confidential and often market sensitive information about clients which, if unprotected, is vulnerable to being exploited by cybercriminals.
The miner retrieves work (i.e. blocks to hash) from the configured server, using a getwork request, performs its hashing on the data, then does another getwork request, this time passing a calculated hash to the server. Upon successfully solving a block, the Bitcoin network would then assign a special transaction contained in each block called a coinbase transaction, which contains the reward, to the address of the Bitcoin client. Also, the reward of 50 BTC given to the successful miner node will change over time; reducing by half every four years to be exact, so that by approximately 2040 the Bitcoin system will stop generating bitcoins.
Customers using Android and iOS versions 5.0.2 through to 5.1.0 of its Copay app are affected, it warned. Monitor lets you view up to 110 of your favourite stocks at once and is completely free to use. Canadian inflation rose 1.1 percent in February from a year earlier as gasoline prices increased for a third straight month, the government said Wednesday. You can expect more of these types of alternative structures surrounding bitcoin to begin multiplying at a rapid rate as money flows into these products in the states, or in Germany or in Sweden. And importantly, the regulatory exemption under which this exists has been applied and has existed for many years and predates crypto, to be sure. It’s not traded on a national securities exchange, it’s not available instantaneously on every platform. It’s traded on the OTCQX, which is an over the counter market, and it’s a different tier of market.
First Macosx Bitcoin Backdoor
Because the transaction is in the block chain, redoing it would mean all miner nodes would have to redo its associated block, as well as all blocks that follow it, since each accepted block contains a hash of the previous one. Hence, this is the Bitcoin system’s solution to the problem of double-spending. Bitcoin Classic eventually introduced the idea of block-size voting, which relies on the principle of a variable block size. It may sound weird but trust me you can make cnbc bitcoin price 2020 coinbase current exchange rate for bitcoin with Telegram. If there was disagreement in the community about the path of a coin, like Bitcoin, for example, then a contentious hard fork would occur.
Cross-platform attacks have already been seen, with OS X threats such as MacOS_X/DevilRobber.A emerging on the scene in October 2011. The time-saving potential of AI platforms, however, depends on the structure of the law firms using them, added Cohen. Large commercial outfits specialising in corporate and finance deals will see more benefits than firms with a broader practice.
Instagram To Block Adults Sending Messages To Children
The first one established was the Bitcoin Market on 6 February 2010, and over the years more exchanges have surfaced, with the Bitcoin wiki listing about 66 exchanges. As previously mentioned, the role of the miner nodes connected to the Bitcoin network is to solve a computationally difficult problem tied with transactions before they are accepted into the block chain.
- In the news, look no further than the recent Microsoft Exchange hack, which saw hackers attack holes in the email server.
- Researchers said they became aware of this campaign when they were called in to assist with incident response and discovered the organization had fallen victim to the ThreatNeedle backdoor.
- To fill this gap, Bitcoin ATMs are rolling out across the country at a rapid pace, offering a more democratic and inclusive alternative to the centralized banking system by providing an accessible gateway to cryptocurrency markets.
- It has evolved over the years, and we’ve seen it modify users’ DNS settings, intercept Internet traffic, infect system drivers, infect 32- and 64-bit system Master Boot Records, as well as download additional malware onto a compromised system.
- Prometei can also act as a backdoor for other payloads, although this behaviour has not been observed in any campaign as of yet.
- Hiddad, which repackages popular apps and sends them to third-party stores, is in last place.
According to Blockchain analytics company Chainalysis, the majority of criminal activity via cryptocurrency is also traceable to a small subset of brokers. This is why leading operators like CoinFlip and Coinsource’s FinCen compliance is so crucial for the industry’s growth.
“We’ve only scratched the surface in what remote working can deliver,” he said. Failure to make this distinction is arguably one of the reasons why blockchain is yet to fully take off, added Halliwell. Another drawback is the staggering amount of electricity currently required to power a blockchain system — a sticky point for many businesses hoping to reduce their energy consumption as part of a wider sustainability push. Despite the new challenges which technology presents, doing things digitally can actually be safer than in-person, said Sanders. For example, the panel recalled cases of lawyers accidentally leaving their phones, laptops and paper bundles behind in taxis and trains, and putting clients’ sensitive data at risk.
Devices enrolled into Prometei’s botnet are then used to mine a number of cryptocurrencies. Prometei is a modular worm used in targeted attacks against Windows Server systems. Written in C++ and .NET, it attempts to enrol devices into a botnet to then be used to mine a variety of cryptocurrencies including Bitcoin and Monero. Kurt Natvig takes us through his analysis of a new sample using the xlsb file format.