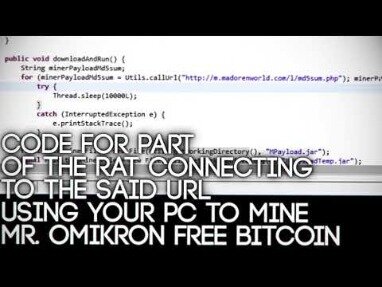
Content
“If automatic updates fail, we encourage users to download and install the security update manually to avoid falling victim to malicious attacks,” Poslušný continues. A malicious cryptocurrency miner is causing havoc in Windows web servers worldwide and those with unpatched systems are vulnerable to becoming part of a mining botnet.

The malicious actors use the name “Los Zetas”, which is an allusion to a Mexican criminal organization regarded as one of the most dangerous drug cartels in the country. Despite that, it is unlikely that the attackers are actually part of this criminal organization.
The authors note that a range of top cryptocurrencies share the Bitcoin core codebase, and a significant number among them are still using out-of-date code, making them potentially vulnerable to the Erebus attack. By showing that distributed permissionless ledgers still rely heavily on the current Internet infrastructure, the paper reminds us that blockchain systems may be insecure against powerful AS-level adversaries.
The mining tools – offered alongside botnet task options such as spam runs or distributed denial of service attacks – put infected machines to use mining Bitcoin. Besides presenting a novel and feasible attack, it shows that Bitcoin is heavily centralised as the majority of the entire Bitcoin network is hosted on a small number of ASes; worse, 3 ASes can intercept roughly 60% of Bitcoin traffic. “These cloud based services do many different things,” said Salazar, “but the purpose is to let developers get something up and running immediately.” “It cuts out all the legwork and lets you build an application as quickly as possible,” added Ragan. “Platform as a service is a commodity that’s in high demand. But if it’s making the life of a developer easier, wouldn’t it also make things easier for a malicious attacker? That’s exactly what we explored.” penetration testers from Bishop Fox, demonstrated a technique for cloud-based bitcoin mining that cost them exactly…nothing.
What Is A Botnet?
Depending on the delivery method and the coding of the bot, they can attempt to spread to other machines to further increase the size of the botnet. The unsuspecting victim of the trojan horse attack will unwittingly open an email attachment or similar file which then covertly deploys the bot onto their machine. Email spam, whereby the botnet machines are used to send large volumes of spam emails in a decentralized way. Similar to spyware, a computer which is jacked into a botnet can be very hard to detect, meaning your company’s computers could be being used for anything without your knowledge.
Guardicore Labs said Wednesday that in the last several weeks alone, the hackers had managed to infect close to 2,000 to 3,000 servers daily. As reported by Hacker News, the botnet has been dubbed “Vollgar” after the vollar cryptocurrency it mines alongside monero , and its “vulgar” way of operating. A malicious botnet has been targeting Microsoft SQL database servers to mine cryptocurrency for two years, according to a new report. This lax approach will inevitably lead to much more devastating attacks, according to cybersecurity veteran John McAfee. Projections from technology research firm Gartner suggest the issue may escalate if security fixes are not implemented by device manufacturers. According to Gartner, there will be more than 20 billion IoT devices by 2020, while estimates from ABI Research put the figure closer to 30 billion.
- Please note that the NCSC maintainsguidancefor securely configuring a wide range of end user device platforms.
- This suggests Prometei may be a combination of a number of underlying tools from disparate creators.
- Economists polled by Reuters had forecast starts would decrease to a rate of 1.560 million units in February.
- Prometei will also attempt to propagate to systems on the network using the same set of exploits used to gain initial access.
It allows any adversary who controls a large enough range of IP address to monopolise all of the victim’s inbound and outbound connections. After occupying enough slots in the victim’s IP table, the adversary triggers the node to restart; then there is a high probability that the victim node will establish all of its new connections to IP addresses controlled by the attackers.
From there, the bot master will use the botnet as a resource from which to deploy various attacks, such as DDoS as discussed above. Rather than relying on a central server, which can be disrupted or disabled by the authorities, a P2P botnet relies only on the devices within the network. P2P botnets are even harder to deal with, because they can be self-sustaining by updating other bots they find on the network.
Fca: Bitcoin Investors ‘should Be Prepared To Lose All Their Money’
With a hefty exchange rate like that, bitcoin mining without the need to devote massive computing resources could be quite lucrative. The company’s findings show that 25% of that malware was active in , and that at least 23 APT groups around the world have used them in attacks.

According to a 2016 study by the security firm BullGuard, up to 185 million devices may be at risk of being compromised by Mirai. Hackers used the network of compromised devices in a series of attacks that caused several major websites to go offline, including Netflix, Reddit and Twitter. IBM researchers discovered a bitcoin mining component in a new variant of Mirai—a form of malware that exploits security vulnerabilities to take control of devices connected to the so-called Internet of Things . People have tried to develop many different attack vectors on cryptocurrencies, from codebase flaws, cryptographic algorithms, mining processes, consensus protocols and block propagation mechanisms to the underlying network layer. Most attacks could be patched quickly by modifying the source code, but preventing attacks that exploit the network layer remains a non-trivial problem as the network layer heavily relies on the existing Internet infrastructure, which is impractical to change. One of their first experiments with their new cloud-based botnet was mining the cryptocurrency Litecoin.
Mirai Iot Botnet Could Be Used To Mine Bitcoins
Botnet activity controlled by malware occurs most often in higher education, with 151 detections per 10,000 devices – five-times the industry average of 33 detections per 10,000 devices, the report said. Cryptocurrency mining is the process of generating cryptocurrencies such as Bitcoin.
This white paper details 7 case studies of attacks that were intercepted and neutralised by Darktrace cyber defense AI, including a zero-day trojan in a manufacturing company’s network. Learn how Darktrace Antigena AI Response modules fight back autonomously, no matter where a threat may emerge, extending to the Cloud, Email and SaaS.
Y Soft is adding to its portfolio of identity verification solutions with the release of a new secure identity verification for networked printers. The race has started between hackers and security professionals following the disclosure of vulnerabilities on Microsoft Exchange Servers, according to Check Point Research. ESET researchers report that the miner leverages a known vulnerability in Microsoft IIS 6.0 to covertly install the Monero cryptocurrency miner on unpatched servers. Mining Litecoins is a low hanging fruit though, low technical barrier and instant money – you don’t have to deal with other people in terms of renting out a DDoSing botnet etc. Other than mining Cryptocoins this distributed super computer could easily be used for other purposes such as password cracking, DDoSing or doing any other large scale parallel task. This is a pretty interesting story, and an interesting use (or mis-use) of cloud resources. We’ve covered similar stuff before like the case when Yahoo! was Spreading Bitcoin Mining Botnet Malware Via Ads, and then more recently when the Pirated ‘Watch Dogs’ Game Made A Bitcoin Mining Botnet.
Researchers conclude, therefore, that botnet kingpins are better off avoiding the Bitcoin mining game and sticking with other techniques. “In a hypothetical example of a 10,000-device botnet, profit without mining is $11,000.00 while profit with mining is $11,007.61—just a $7.61 gain,” the company wrote. According to researcher estimates, a botnet controller attempting to mine Bitcoin with a 10,000 system network would initially see a net loss in operations and with increasing difficulty cycles productivity would plateau off without turning much of a profit. “But even if we allow a zero cost for hardware and power , the difficulty level of common mining algorithms and the nonspecialized hardware that the malware infects make this a futile effort.” It is shown that the attack is feasible for large AS/ISPs, only needs a few weeks of execution and can be executed with a trivial traffic rate.
He mentioned examples including logic puzzles, validation by credit card, and even live operators. It does seem clear that any cloud servce without significant anti-automation is likely to find itself harboring more botnets than real users. During the course of the experiment, a number of services revised their verification systems to defeat automatic creation of accounts. “At this point we can do things like DDoS, crypto-currency mining, data storage, and more,” said Ragan. “As penetration testers, having a distributed botnet under our control was the goal.” Having a tame botnet to launch white-hat DDoS tests against willing clients was definitely valuable. While cloud migration isn’t simple, it can be enabled and improved using the right security tools. The COVID-19 pandemic is pushing organisations of all sizes to up their security game, for one implementing Cyber threat intelligence programmes.
The idea of a computer being assimilated into a network and used for nefarious purposes sounds like something out of a science fiction movie. In this article, we continue our focus on malware with a look at the concept of a “botnet”. This category only includes cookies that ensures basic functionalities and security features of the website. The operators of the malware have constantly been adapting to takedowns and other setbacks to ensure the continuity of the campaign. In December 2020, Seaman noticed the presence of aBitcoin walletaddress in newer variants of the malware, along with some other details. “In examining these additions further, it became clear the wallet data being fetched from the API was being used to calculate an IP address. This IP is then used for persistence and additional infection operations,” notes Seaman inhis analysisof the malware.
Interestingly, Prometei’s module are constructed differently based on their purpose, with all mining operations written in C++, whilst propagation and credential harvesting functions are .NET based. This suggests Prometei may be a combination of a number of underlying tools from disparate creators.
They conclude that it is possible to isolate roughly half the mining power by hijacking less than 100 prefixes. They also show that a large number of hijacks targeting Bitcoin nodes are happening regularly (however, a longitudinal analysis in below found that this kind of hijacks is just misconfiguration). Some deployable countermeasures were proposed, including both short-term and long-term patches. This is a control-plane attack, which utilises the routing manipulation to intercept Bitcoin traffic from/to the victim nodes directly.
News Corp Cuts Deal With Facebook In Australia
While the attackers were active around the end of August, there has been no further activity from them and no further infections reported. “Features such as untraceable transactions and a proof of work algorithm called CryptoNight, which favours computer or server central processing units, make the cryptocurrency an attractive alternative for cybercriminals. Bitcoin mining, in comparison, requires specialised mining hardware,” he explains.
The bot is propagated by sending a malicious shell script to a compromised device that then downloads other scripts. After the victim device executes the downloaded scripts, it starts waiting for commands from its Command and Control server.
The hacker duo used an automated process to generate unique email addresses and sign up for those free accounts en masse, assembling a cloud-based botnet of around a thousand computers. “Students’ online activities through the use of untrusted websites that host crypto-mining malware could represent the indirect weak backdoor to attack universities’ high-bandwidth capacity networks,” Alfrmawi said. “This is not surprising as Asia has long been one of Bitcoin’s biggest supporters with Japan, South Korea and Singapore being the world’s largest Bitcoin market,” ICT expert Hamza Alfrmawi told University World News. “Crypto-mining activities on universities’ open networks make them work abnormally slowly and make it easy to be attacked by cyber-criminals,” he said. These early threat indicators usually precede other stages of an attack and are often associated with opportunistic botnet behaviours, explained Vectra’s 2018 RSA Conference Edition of its Attacker Behavior Industry Report published on 29 March. As the value of cryptocurrencies rise, hackers exploit laxer controls of university computer networks to mine cryptocurrencies. Attacks can include leveraging devices “for external gain, such as Bitcoin mining or outbound spam”, according to the report from Vectra Networks, a United States company whose products monitor network traffic for cyberattacks while they are in progress.
Although not considered by experts to be as dangerous as a targeted cyberattack, cryptocurrency mining still puts personally identifiable information, protected health information and financial data at risk, says Vectra. Open computer networks consisting of more than two million devices at some 100 Asian universities were targeted, with hotspots in Singapore, Japan and South Korea.
After all, if someone is using your fleet of machines to relentlessly hammer a server across the globe, your network is going to show it. Okay, so, by this point, you’re probably seeing why botnets can be such a nasty form of malware. They aren’t even malware, strictly speaking, but rather a delivery system for other forms of malware. Even worse – the owners of the computers often have no idea that they’ve fallen victim to the attack.