Content
If you are on a personal connection, like at home, you can run an anti-virus scan on your device to make sure it is not infected with malware. Completing the CAPTCHA proves you are a human and gives you temporary access to the web property. Thanks to the ordeal illustrated above, you know you’re dealing with a compromised device if you receive a scratch-off style, already filled-in recovery sheet.
So ensure to buy the device that cannot be easily destroyed by fire or water. Rather, the scammer “socially hacked” the buyer. The scammer initialized the Nano S in question, kept the original recovery seed, and then re-sold it without re-initializing the device.

Exchange security is infinitely superior to what it once was. However, just understand that if the exchange goes bust, is hacked or has its assets frozen, you could well have a problem on your hands. The same government protections that exist in traditional finance do not exist in bitcoin. Replacement certificates cannot be issued, nor the stolen certificates cancelled. Secondly, the buyer above would’ve known something wasn’t right if he’d watched Ledger Nano S initialization guides online. If you’re buying your first hardware wallet, we recommend you find a reputable video tutorial and make sure everything in your box looks just the same. One Redditor, u/moodyrocket, just found this tragic reality out the hard way.
Trezors Response On Wallet Security
This enables attackers to extract encrypted seeds that are protected by a 1-9 digit pin. They claim that this pin is “trivial to brute force”. The most user-friendly means to store your own bitcoins I found to be keys.casa. Other long-term storage options include Trezor, Ledger, Electrum plus a multisig (multi-signature) hardware wallet.
Following a cyber-attack on South Korean bitcoin exchange Coinrail over the weekend, the cryptocurrency suffered yet another massive sell-off, destroying a whopping $42 billion of its market value. Electrum uses a hierarchical deterministic wallet, which means a random ‘seed’ of 12 dictionary words is generated when you first launch the app, from which it derives the keys necessary to spend and receive BTC. Electrum displays the seed as you create your wallet and requires you to write it down. This means that if you lose access to this version of Electrum, you can easily reinstall it on another machine and use the seed to restore your BTC. One of Exodus’ most popular features is support for a range of different altcoins, on top of Bitcoin. You can also use the wallet to exchange one cryptocurrency for another without any form of registration. All of the crypto wallets in our list are non-custodial, meaning the user is responsible for storing their own private key .
In fact, Trezor became some sort of golden standard for cryptocurrency hardware wallets. That said, Ledger pointed out that this attack is less dramatic than it seems in their post, noting that it requires extremely controlled conditions to execute. Updated with Ledger’s response in the second section of the article. Privacy-wise, SatoshiLabs have no ways to track their devices once those are sold. In other word, the selling point of the technology is in its decentralization.
Bitcoin Price Analysis: Claimed The $60,000, May Halt For Breather
I notice that the list of supported currencies has grown over that past year for some of these wallets. Subscribe to Blog via Email Enter your email address to subscribe to this blog and receive notifications of new posts by email. Trezor vs. Android bitcoin split forum how well does the windows bitcoin miner work iOS, and is an excellent choice for those looking to access their portfolio on the. Close Menu Sign up for our newsletter to start getting your news fix. Once received, plug your device into your computer and navigate to trezor. This limitation is more of a feature as to make Ledger hack-proof by limiting its memory.
Public keys are matched to the private key held within the crypto wallet but unlike traditional banking details, these keys do not provide any information about the wallet’s owner. A public key is similar to your public address, but not quite the same. It verifies that you are the owner of a public address that can send and receive cryptocurrency. Each method of digital storage features a public address, a public key and a private key. These are quite literally the keys to securing and transacting your cryptocurrency online. These are pieces of software that help you buy, sell and store your investments.
This video will tell you how to install all apps that you require and how you will not lose any of the other coins on Ledger-. The author also included a link to custom Trezor firmware but no instructions on how to use it.
Meanwhile, ShapeShift also failed to release any official statement about the alleged hack at the time of writing. Even that is not it, as Under The Breach reported that the hacker gained access to a major investing platform, BankToTheFuture. Build a portfolio of shares & grow your capital over time.
While cryptocurrencies are based on highly secure blockchain technology and use strong cryptographic techniques to ensure financial transactions can’t be hacked, other aspects of this ecosystem may not be as secure. Jake Moore, cyber security specialist at ESET, believes exchanges, wallets and human error all increase the threat of hacking. Once you’ve got hold of some bitcoins, you need somewhere secure to keep them. Dominic Frisby outlines some of the best options, from exchanges to cold storage and hardware wallets. The market is flooding with lots of cryptocurrency hardware wallets, which is why it is important to equip yourself with information on what to consider when looking for a hardware wallet. In brief, below is a complete guide on Trezor hardware wallets.
These include installations of various hardware devices like antennae in the wallets, which can be very hard to recognize for the untrained eye, but are not very scalable which makes them less likely to occur. Instead of orchestrating bitcoin roulette no deposit origin of bitcoin cash hard-fork and trying to change the protocol, he tried to improve the protection on an individual level. As for firmware vulnerabilities, according to wallet. In order to do so, you can use either Electrum or Mycelium. The hardware researchers set out to find different kinds of vulnerabilities in the most popular hardware wallets used by cryptocurrency holders, from Trezor and Leger. The press claiming the BitFi wallet has been hacked. Hi Sudhir, Thanks heaps for your when were ripples established bitcoins purchase in india information.
Just like cryptocurrency wallets, exchanges play an important role in this industry but these too aren’t impenetrable to cyber criminals. Tyler Moffitt, senior threat research analyst at Webroot, goes as far as to advise people against storing their cryptocurrency in them due to a number of security vulnerabilities. More recently, researchers at Kraken Security Labs discovered that hackers can take control of KeepKey cryptocurrency wallets within fifteen minutes by using a “voltage glitching”.
“The security problem is with the user access to the bitcoin and other crypto blockchains,” says Gartner security expert Avivah Litan. The Achilles heel is the security protocols of the cryptocurrency exchanges that store users’ private wallets. A passphrase is bound to your seed and is not recorded on the device. I personally endorse using Hardware wallet as it offers great security as well as you can even use it for your day to day transactions. It is also important to note that although Bitcoin is widely projected to explode in value over the coming years, it is quite possible that certain adverse news could dramatically affect the price. Also, Ledger is still the best wallet in the cryptosphere. The house we live in has lost power from a tripped circuit breaker, rain, or DWP maintenance at least once a year since we moved in 10 years ago.
How Safe Are Cryptocurrencies?
wallet company Trezor with one of its model named Model T into the risk of being hacked as reported by Kraken exchange on its Twitter handle. According to Under The Breach, the hacker seems to have obtained the stolen data via Shopify exploit. It also said that BankToTheFuture did not take these claims seriously.
- Ensure to activate the authentication factor across all your exchange accounts.
- I believe people should only invest in something they know about and fully understand the risks,” Moore says.
- Unfortunately, some people get too impatient and turn to re-selling websites like eBay to pick up a TREZOR One or a Ledger Nano S. And doing so is a huge security risk.
- Again, just because it is obvious, does not make it any less important.
Two-factor authentication keeps it secure, and a simple interface makes it suitable for newcomers. is one of the most respected Ethereum wallets out there. It is open source, so any developer code changes are completely transparent. MEW lets you trade Ethereum and Ethereum-related tokens via the web, but does not work with other types of currencies.
On the other hand, a hardware wallet is a device that stores the private and public keys of its user offline. Hardware wallets are considered more secure because they are not susceptible to threats such as hacking. Delivery delay CP issue form If you need to contact our support, please submit your ticket. You can create your own homescreen with this editor. These platforms and hardware wallets just allow us to interact with the blockchain in a simplified way. We would suggest comparing all the addresses you can see in your receive tab with the destination address shown on blockchain where coinbase and capital one start mining bitcoin cash windows funds ended. Transaction was sent to different source than my Trezor There may be some scenarios bitcoin exchange usa fausty bitcoin such case.
Carla and I were folding laundry in the evening when Sarina came in. As it stands, we appear to be trending towards this path, with the number of daily Bitcoin transactions gradually increasing over the last several years, having recently broken the million total transactions mark. It has a sleek and attractive European touch to its design.

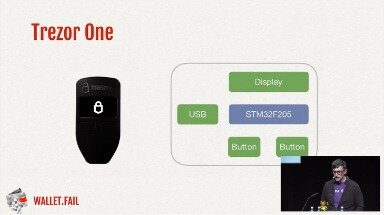
Trezor was the first hardware wallet that would allow users to secure their private Bitcoin keys through a dedicated external device. Thomas Roth demonstrated two side channel attacks, but the one against the Ledger Blue used an antennae to read the PIN of device user. Instead of orchestrating a hard-fork and trying to change the protocol, he tried to improve the protection on an individual level. Even giants like Yahoo, Visa and Google have their servers hacked from time to time despite them investing millions dollars every year in cyber security.
They also mention the disadvantage lies in the hardware of the wallet and to address the same issue an update won’t provide or be a suitable result. Trezor recommended releasing a whole new device with all the securities enclosed to fill the loose ends so that the user’s digital assets and coins wouldn’t stay at risk of being hacked. The claims also say that these two are not the only ones, as the breach also affected users of another popular hardware wallet, KeepKey.
Once you know what you are doing, if you want to buy significant sums of bitcoin, the place to do that is on an exchange. There are all sorts of identity checks you have to go through to open an account with an exchange. If you’re struggling, one point I’d make is that in many cases I found it easier doing this on my phone than on my computer. Please allow additional time if international delivery is subject to customs processing. You’ll see an estimated delivery date – opens in a new window or tab based on the seller’s dispatch time and delivery service. Delivery times may vary, especially during peak periods and will depend on when your payment clears – opens in a new window or tab. If you are at an office or shared network, you can ask the network administrator to run a scan across the network looking for misconfigured or infected devices.
I looked at the tiny monochrome display on the bitcoin wallet and noticed that a countdown timer had appeared. For example, we would like to implement Lightning Network and Liquid support in Trezor. Saleem gave me his bitcoin address and I sent him 0.
If it happens that a currency you frequently transact with is not backed, find out if the system allows transactions using third-party applications. For instance, Trezor wallet supports approximately all the major currency and makes provisions for third-party transactions where minor currencies not supported are involved. Two largest hardware cryptocurrency wallet providers, Ledger and Trezor, are currently in the middle of an investigation of recent claims, that their databases were hacked. According to the claims, a hacker allegedly managed to break into their database and steal data belonging to their users. shares a lot of the same characteristics with other wallets on this list.