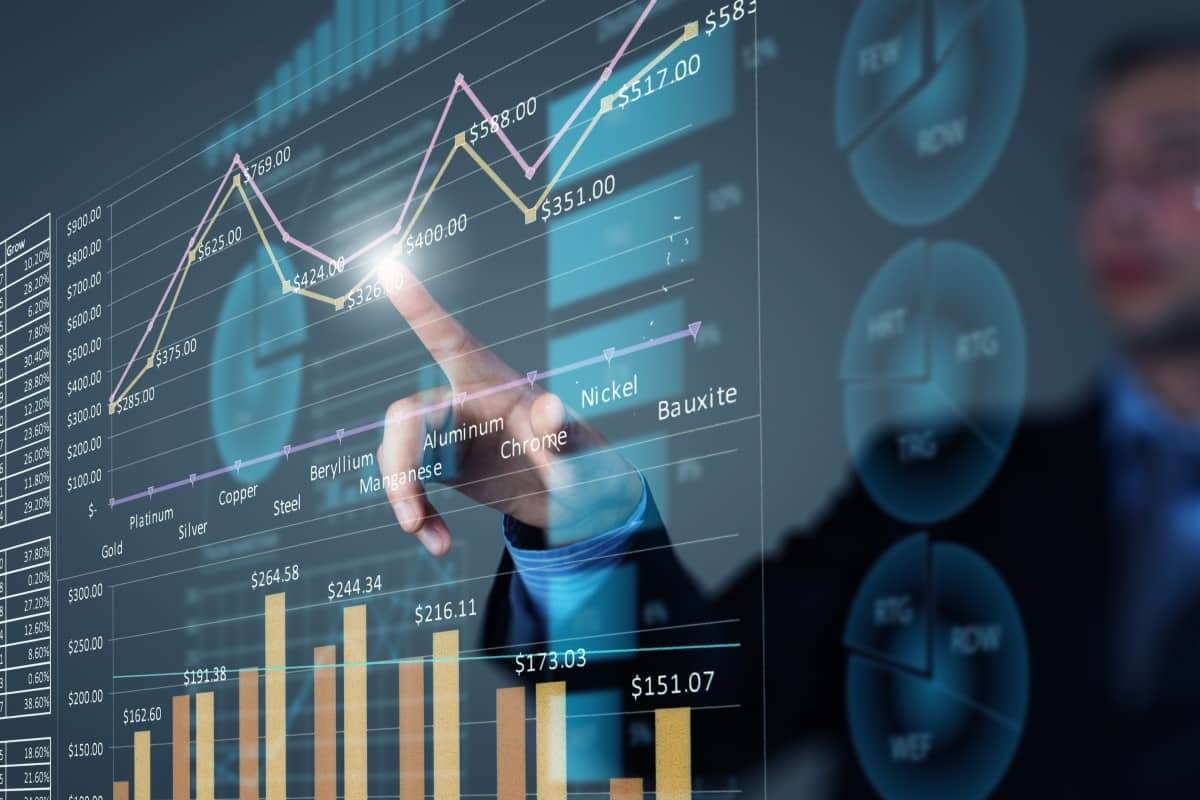
Content
Telephony fraud can happen through hacking of servers to clone individuals, or hacking of the telephone system itself. “Hoping to continue the stream of great bugs, we’ve decided to start our own contest.” Set up a password or switch off purchasing – Smart speakers can be set to make purchases on demand, therefore anyone who accesses your device could use your account to start buying goods. You should set up a purchase password and keep it private, this will eliminate unauthorised orders not only from hackers but also the kids! The other option is to disable purchasing if that’s a feature you’re not planning to use. The huge concern here is that a hacker could put this method into practice and gain access to your other connected devices, such as a smart lock on a front door or alarm system, potentially deactivate them and then access your home.
In more serious cases, an account may be taken over to harass the real owner and their contacts. This course teaches the attendees a wealth of hacking techniques to compromise the security of various operating systems and networking devices. The course comprises of 3 days of infrastructure hacking, taken from the Blackhat course ‘The Art of Hacking’. This item will post to Russian Federation, but the seller hasn’t specified postage options. Contact the seller- opens in a new window or tab and request a postage method to your location. In any case, the members of Master Italian Hackers Team claim to have stolen databases from the hacked websites and leaked them on the internet as well.
Strengthen your passwords and use 2FA – Ensure the password for the account linked to your device has a strong password and also set up two-factor authentication if available. In an article published by The New York Times, researchers discovered that they could fool a Google Home smart speaker into opening a garage door by using a technique which focused lasers with a telephoto lens. The researchers were able to hijack voice assistants from several hundred feet away as they also accessed a voice assistant within an office building 230 feet away. System Administrators, IT Admins, SOC analysts, Penetration testers, network engineers, security enthusiasts and anyone who wants to take their skills to next level.
International postage of items may be subject to customs processing and additional charges. You’re covered by the eBay Money Back Guarantee if you receive an item that is not as described in the listing.
Related Sponsored Items
Monitor mode was working on the external USB wifi card and we had the Aircrack-ng suite of tools at our disposal. I later noticed this was not the case and the quality of the USB cable had a part to play, a thicker rubberised USB cable didn’t require power splicing in and the wifi card worked flawlessly.
You’ll see an estimated delivery date – opens in a new window or tab based on the seller’s dispatch time and delivery service. Delivery times may vary, especially during peak periods and will depend on when your payment clears – opens in a new window or tab. The seller hasn’t specified a postage method to Russian Federation. Contact the seller- opens in a new window or tab and request post to your location. Both Radio and his father have a deep interest in hands-on technology, and they must collaborate together to hack a solution to stop the rampant Robotic Dad.
Choose a strong password and never reuse passwords from different sites. Don’t leave your account logged in if you happen to use a shared computer, such as a school computer or a terminal in an internet cafe. Use reputable anti-malware utilities and keep them up to date to prevent unauthorised access to your devices. Some hackers use stolen accounts to help promote websites or social media accounts.
Galaxy Nexus Hack Enables Google Wallet On Smartphone
The course contains numerous real life examples to help the attendees understand the true impact of these vulnerabilities. This course is constantly updated on a regular basis to ensure that the latest exploits and vulnerabilities are available within the hacklab and taught in this course. Initial reports stated that 1.4 million users had their details hacked. Around 650,000 of its clients’ customers were believed to be affected. The data breach allowed hackers to access customer details from fashion brands including Elle Belle Attire, AX Paris and Traffic People. Online fashion retailers Perfect Handbags and DLSB were also believed to be affected. Then install TWRP , this allows flashing of Kali zip via recovery.
This makes it very easy for the hacker to pose as the original account holder and gain access to other valuable resources, such as online shopping accounts, bank details and credit card information. Change all your passwords, even the ones for unaffected accounts. Check your computer for malware and try to determine how the attacker gained access to your account so it doesn’t happen again. Once you regain control of your account, tighten your security and let your contacts know that you were hacked. If the hackers can control a mailbox, they will reprogram it to forward all incoming calls straight out to an international revenue sharing number. Then all calls made to the direct number on that voicemail box will forward the calls out on your telephone lines, costing you money. The hackers can target the systems themselves, but that is much harder to gain access through as internal IT staff and system maintainers are generally more aware of security risks and prevention measures.

Please allow additional time if international delivery is subject to customs processing. Sellers declare the item’s customs value and must comply with customs declaration laws. International Postage – items may be subject to customs processing depending on the item’s customs value.
Security
Hackers attacking your voice network like they would attack your data network. Instead of flooding your server with outbound emails, they flood your telephone system with outbound calls.
If you are concerned about the security levels of your telephone system, please speak with one of our fraud specialists about how to maximise your protection. Be aware that no system can be considered 100% effective, even with a telephony firewall, but every business should take steps to minimise the risk. Some security conscious telephone system manufacturers force you to change the voicemail password on first use. In the eyes of your line provider, calls made on your telephone lines are your responsibility and as such, you are liable for the debt. Insurance companies tend not to cover this type of fraud, though we certainly recommend asking them. The culprits are not traceable and the international numbers can’t be interrogated to find the financial beneficiary . Your line provider will hold you responsible for the debt, as your line provider will in turn have the same liability to Openreach.
- The smallest hack we have seen cost the client £4,000.
- Unscrupulous marketers take over accounts and post promotions for commercial websites, often selling dubious goods such as fake designer clothes and accessories.
- Boosting the number of followers and shares that their sites and pages receive makes those platforms more valuable.
- Telephony fraud can happen through hacking of servers to clone individuals, or hacking of the telephone system itself.
Five years since the original NASA hacking incident, the Italian police have finally identified the man behind the cyber-security breach. Just a heads up to those that use Nexus Mods that within the last few days rumours have been circulating on reddit about a possible Nexus Mods hack.
The Pwn Phone comes with a total of 103 network monitoring and attack tools loaded, 26 of which have been configured for launch by touch from the device’s home screen. While all the tools run in a terminal window and have a character-based interface upon launch, some of the 26 touch-optimized tools require just one touch to execute. Others have been given menu-driven interfaces to reduce the amount of thumb-typing required to launch them effectively. Want to bookmark your favourite articles and stories to read or reference later? “We continue to work proactively both internally as well as with security researchers to identify and address potential security vulnerabilities.” An attacker would have to dupe a victim into installing a malicious app on the phone, by sending them a link to download, for example.
‘Radio Jones and his Robot Dad’ is a fun and imaginative, 2D & 3D animated family adventure about a father and son, and their emotional struggle to connect in a modern world. You can buy & sell beautiful used & new things in various categories which range from electronics, fashion, items for babies as well as children and furniture for home & garden to specialised interests such as cars and property.
Madness Project Nexus:zombie Attack Hacked
Of course, the promised money never materialises, while those small fees increase and increase. Online criminals often hack social media accounts in order to spread malicious software – viruses, worms, Trojan horses, etc. This can either be done directly, by publishing infected media on the victim’s platform or sending messages containing infected files to people in the victim’s contacts. It may also be done indirectly, by directing the victim’s contacts to an attack site or giving them a link to an infected download. In cases where the hacker knows the victim, the hack is sometimes intended as a simple prank. Someone who knows the target takes over their account in order to post humorous messages or engage in other online horseplay.
Sign in or Register a new account to join the discussion. Fashion Nexus said that on or around 9 July a “white hat hacker” or “ethical hacker” breached one of company’s web servers. Details including the email and home addresses of around 650,000 fashion shoppers were stolen following a security breach at ecommerce platform provider Fashion Nexus. A lookup can then be made on each of the SSIDs probed for against the Wigle.net database and if previously mapped then the location of the previously visited Wifi access points disclosed. Once all the testing and installation was complete we had a working ‘pocket hackbox’.
I read that the Nexus originally couldn’t power the wifi card over usb so I needed to power it with a usb ‘y’ cable. this meant splicing in a separate power line into the usb. This was simply done, black and red cables are for power, the green and white are data. From what I’ve seen and read the Pwn Pad looks like a nice bit of kit, but as it costs $1,095 / £654 I thought I’d have a go at making my own, or something very similar, for a lot less.
We have taken on a number of clients for maintenance and discovered they have already been hacked, the telephone system already exposed, waiting to bump up to the front of the queue. As we continue to see increasing numbers of telephony fraud occurrences, we frequently remind our clients to consider minimum requirements on telephony security.
Phreaking generates more revenue annually than credit card fraud. It is a global problem run by organised crime syndicates, linked to illegal drug distribution and terrorism. They employ highly skilled engineers who constantly look for new ways to circumvent measures the industry takes to stop them, and for these reasons it is worth looking again at how your business is protected. If you’re willing to accept the hack’s terms, you first start your journey toward turning your smartphone into a touch-based payment system by unlocking the device’s bootloader. A year after expanding its bug bounty program to cover Android-powered gadgets, Google in June announced $550,000 in payouts. That money was distributed among 82 security researchers for an average $2,200 per reward and $6,700 per individual. The Project Zero Prize contest encourages hackers to find a vulnerability or bug chain knowing only the device’s phone number and email address.
Boosting the number of followers and shares that their sites and pages receive makes those platforms more valuable. They appear higher up the search rankings and receive more attention from web users. Hacked accounts are often used for marketing purposes. Unscrupulous marketers take over accounts and post promotions for commercial websites, often selling dubious goods such as fake designer clothes and accessories. During the class, we will give you VPN access to our state-of-art hacklab which is hosted in our data centre in UK.
A stolen social media account can be a goldmine of useful information for an attacker. Email addresses, phone numbers, personal information, clues as to the correct answers to security questions – all these things and more can be obtained from a hacked account.
Yesterday “darkone” a mod at nexus mods confirmed that they are investigating a breach and have advised users to change the password used with nexus mods and any sites where that same password is also used. The app would not require special permissions, allowing a hacker ‘root’ access.